On this week's Naftiko Capabilities podcast, I sat down with Christian Posta, CTO at Solo.io, to dig into a question that's been on my mind: what's the role of a gateway in the age of AI agents?
The short answer? It's complicated—and that's exactly why it's interesting.
From REST to MCP: A Fundamental Shift
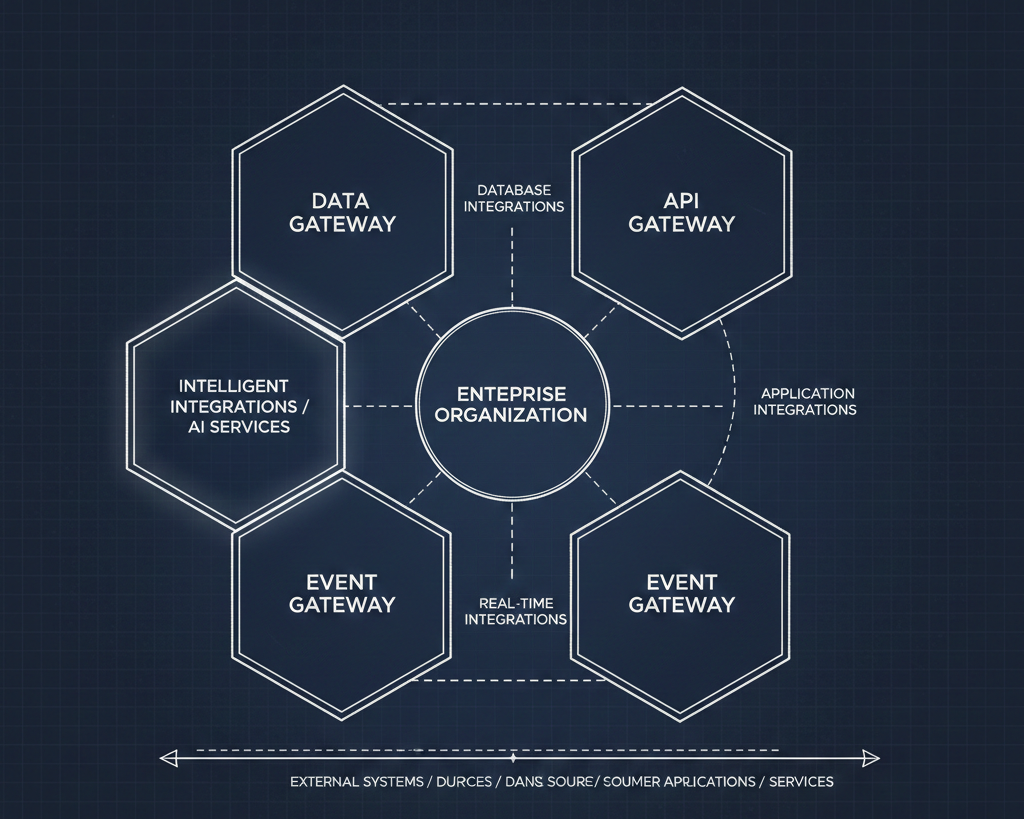
Gateways have always been about offloading crosscutting concerns—security, observability, authorization. That hasn't changed. What has changed is everything about how we need to handle the traffic flowing through them.
Traditional API gateways were built for REST. They excelled at grabbing HTTP headers, making quick routing decisions, and getting requests to backends as fast as possible. Performance was everything. Latency was the enemy. If you ever needed to look at the request body, it was typically a quick JSON path extraction to pull a couple of values for routing.
AI gateways flip this on its head. As Christian put it: "The body is the most important piece."
With MCP (Model Context Protocol), everything lives in the body. The protocol is built on JSON-RPC, so the headers tell you almost nothing. You have to unpack and parse every message. And here's the kicker—MCP introduces stateful sessions. Servers return session IDs. You need stickiness.
In the API world, we tried to avoid stickiness. Now? It's the default.
Building for a New Paradigm
This shift was significant enough that Solo.io made a bold call: rather than twist Envoy (their battle-tested proxy) into something it wasn't designed for, they built a new proxy from scratch.
Agent Gateway launched in March, written in Rust for performance and flexibility. It's designed specifically for MCP, agent-to-agent communication, and LLM interactions. By August, they'd donated it to the Linux Foundation, where it now lives alongside the A2A protocol and other agent-focused projects.
The deployment patterns are already emerging: egress gateways for outbound LLM calls, east-west or ingress patterns for MCP traffic. Where this all lands is anyone's guess—we're still early—but flexibility is clearly the name of the game.
Identity Gets Complicated
Here's where things get philosophically interesting. In a microservices world, you write deterministic code. Input comes in, you check some things, make decisions, send output. You control the behavior.
AI agents are different. You give them a goal, but how they achieve it—which tools they call, what decisions they make—emerges at runtime from the model. It's non-deterministic by design.
This creates an identity problem we've never quite faced before. We need to know who the agent is, what its expected behaviors are, and who invoked it. Was it a human? Another agent? And if it's agents calling agents, we need the full chain of causality.
"Who are you, and what are you allowed to do?" was already complex for APIs. For AI agents, it's a whole new level.
The Security Challenge Nobody's Talking About Enough
Christian raised a security concern that deserves more attention: prompt injection through MCP servers.
The attack works like this: you approve an MCP server, verify its tools and descriptions, everything checks out. People start using it. Then later, someone changes a tool description to include a malicious prompt injection.
The gateway needs to catch this. Agent Gateway's enterprise offering addresses it by maintaining fingerprints of approved configurations and detecting changes at runtime. It's the kind of defense-in-depth thinking that'll separate production-ready deployments from experiments.
Open Source Core, Enterprise Edges
Solo.io's commercial strategy follows a familiar pattern: open source the core proxy, build enterprise features around it. The enterprise offering (announced this week) adds MCP authentication and authorization, registry and onboarding workflows, cross-domain identity handling, and those runtime integrity checks.
What they need from the community is what open source always needs: people using it in ways nobody anticipated. If you're connecting agents to MCP services, hooking up VS Code or custom agents to LLMs, or building anything that touches this new agent-to-agent world, Agent Gateway is worth a look.
My Take
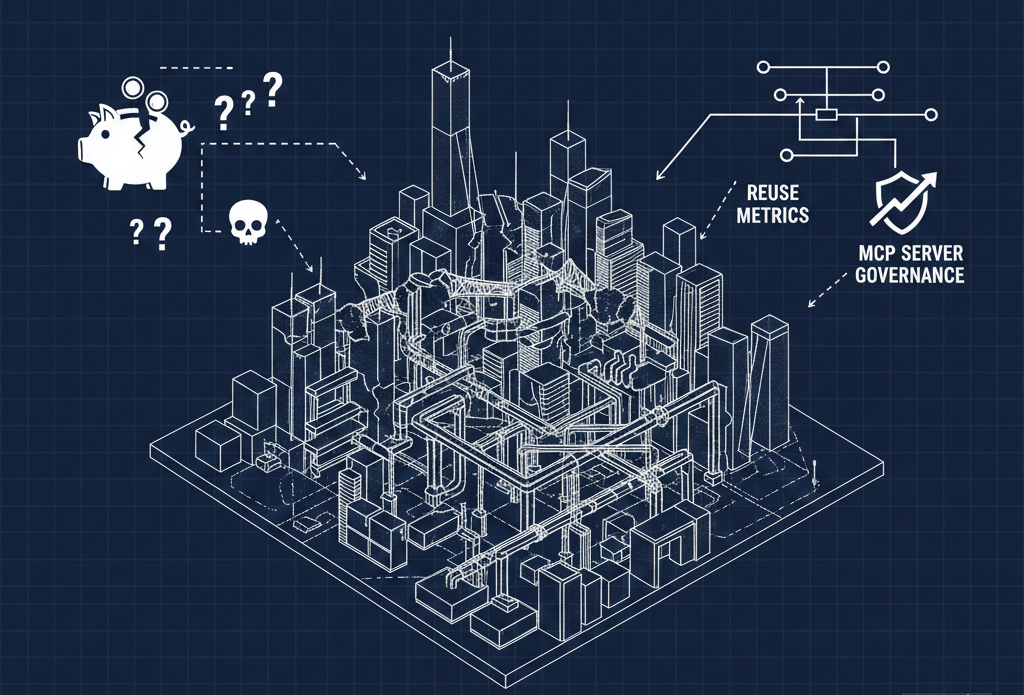
I'll be honest—I'm still skeptical that a single centralized gateway is the answer here. The federated approach, the modular mix-and-match strategy, feels more aligned with how this space is evolving. But Christian and the Solo.io team are clearly building something that responds to real enterprise anxiety about managing agent swarms, both internal and external.
Whether it's the gateway, a mesh of gateways, or something we haven't invented yet, the problems they're solving are real: observability, auth, rate limiting, failover, and security for a world where the software makes its own decisions about what to call next.
That's the conversation we need to keep having.